Basics of Bug Bounty and Reporting at BugéDex !
BugéDex: A hands-on cybersecurity workshop by CSI-VIT and CloudSEK
I had recently attended a workshop organized by the Computer Society of India - VIT Student Chapter in collaboration with CloudSEK . This was an introductory hands-on cybersecurity workshop that introduced the attendees to the art of bug bounty and technical reporting. The workshop itself had a lot of traction and brought with it a wave of questions from my friends and colleagues who were not able to attend the workshop but were still curious and interested to dive into the world of cybersecurity. So I figured I’d pen my thoughts, sharing my experiences and take aways from the workshop by writing a blog.
Firstly, here's the flow for BugéDex:
In the workshop seminar we discussed:
- Introduction to Bugs.
- Deep Dive into Security Bugs.
- How to report a bug by writing a technical report
In the hands-on session:
- Saw a vulnerability finding in an app from my college.
- Scanned an app of my choice.
- Asked to find a vulnerability and deep dive into it.
- Reporting my finding.
The Seminar
Firstly, I was introduced the basics of what was going to be taught, we started with what a bug was. So what's a bug ? A bug is an element in the software or hardware component, that leads to an unexpected outcome. Bugs aren't necessarily bad elements, they can sometimes turn out to be great features or become the cause for the worst kinds of disasters. In the workshop, we saw a few examples of bugs, one of them being a bug in the mars orbiter that resulted in a loss of several million dollars, this bug was due to the changes in the metric system, another one was a bug in The Vancouver Stock Exchange, that had again resulted in financial loss for the people invested in the stock market, this was a rounding off error. From these examples we understood that bugs lead to quite expensive outcomes and they can be hard to eliminate completely. We saw a few other examples of bugs before we moved on.
As we now knew about the basics of bugs, we next saw how these bugs arise. Mr.Shahrukh took over the talk and discussed on the process of building an application and the importance of testing and how it directly relates with the success of the application and how all this is done to make the whole experience pleasant for the end user, this is the main end-goal of a developer. He also spoke about internal applications and how they're mostly not tested.
Next up we were taken for a shallow dive further into testing, where we learn about the different types of testing :

If an application passes most of these tests, it's assured that it's good enough to be used by the general public.
Next, we saw the reasons for testing, and learnt about what we get out of the whole testing process. Mr.Shahrukh briefed us about the different testing environments, this was very interesting and insightful because I know that I'm going to be learning about these in my future courses. Mr.Shahrukh also took the time to answer the questions that other attendees had, although I personally didn't have any questions, listening to the answers of others' questions did make things more clear for me and in many cases, I personally didn't know the answers for these questions, they made me realize that these were the doubts I had without even realizing that I had them as well, hence it was very exciting to hears these questions getting answered.
After answering all of the questions, Mr. Shahrukh took us to the world of bug reports, here, he explained us, how critical it was to report the bugs we come across as they can help the developer correct them at the earliest. He also differentiated between the contents of a bad bug report and a good bug report, the end-goal here was to make the developer aware about the issue in a very simple way so that they can understand and resolve it with lesser difficulties.
A few aspects that lead to a bad technical bug report are:
- lack of proper details about reproduction steps
- lack of evidence for the issue
- lack of proper explanation for the issue, if it's complex
A few aspects that lead to a good technical bug report are:
- Explaining your observations in the simplest words mostly
- Explaining the affected component
- Providing proper evidence
- Being friendly and supportive
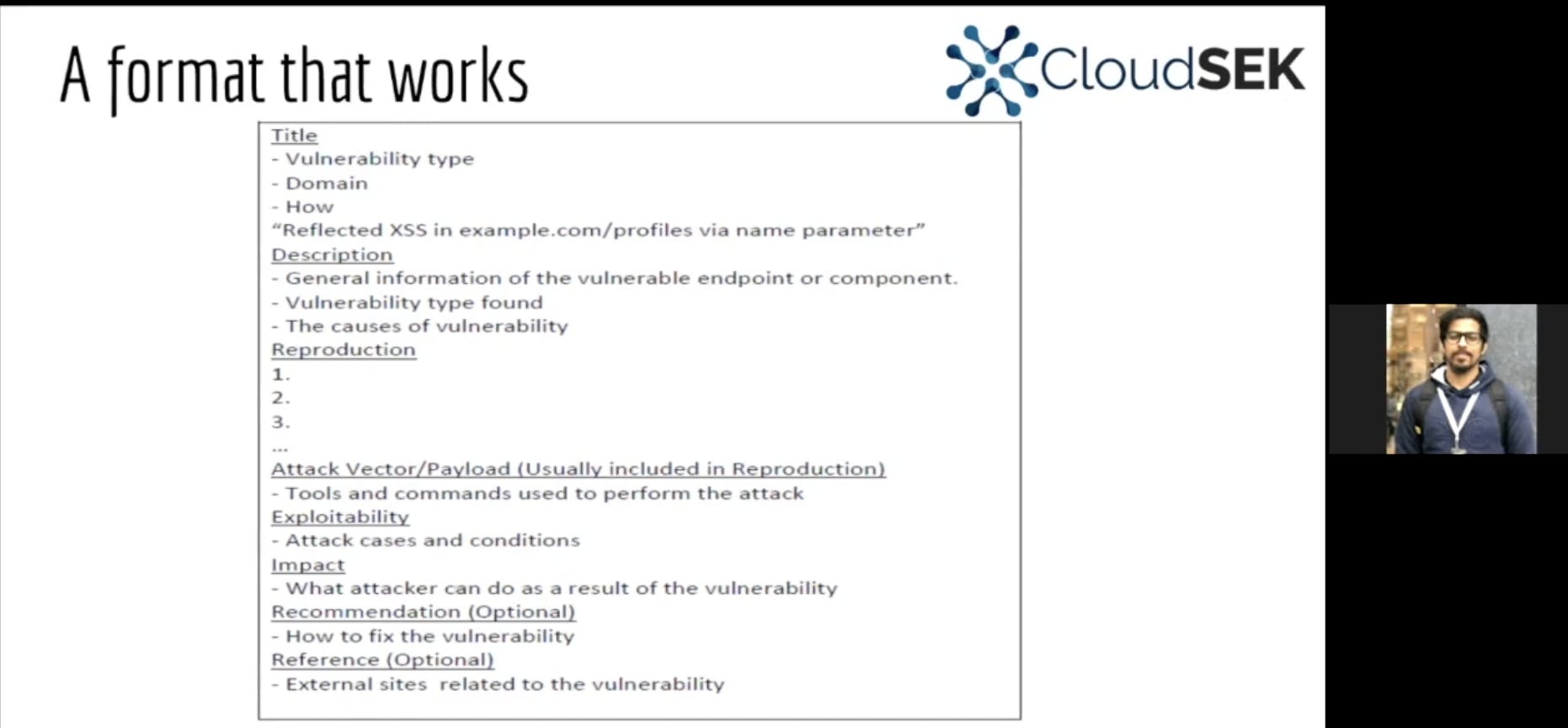
We also learnt about the triage process in brief. Next, Mr. Shahrukh, explained us about the format a bug report can have;
After this, Mr. Sudipta took over and he gave us an introduction to OSWAP (Open Web Application Security Project) Top 10 List. This list has been maintained for several years, this list contains the top 10 most prevalent vulnerabilities in web applications. There is an OSWAP Top 10 List for mobile applications too, although this hasn't been updated since 2016, it is still very relevant.
After a proper introduction on what OSWAP was, Mr. Sudipta showed us the OSWAP Top 10 List for Web Applications, and briefed into the first few vulnerabilities, it was interesting to see the different kinds of vulnerabilities that are out there. He took a deep dive into injections and injection attacks.
We learnt about the different kinds of injections.
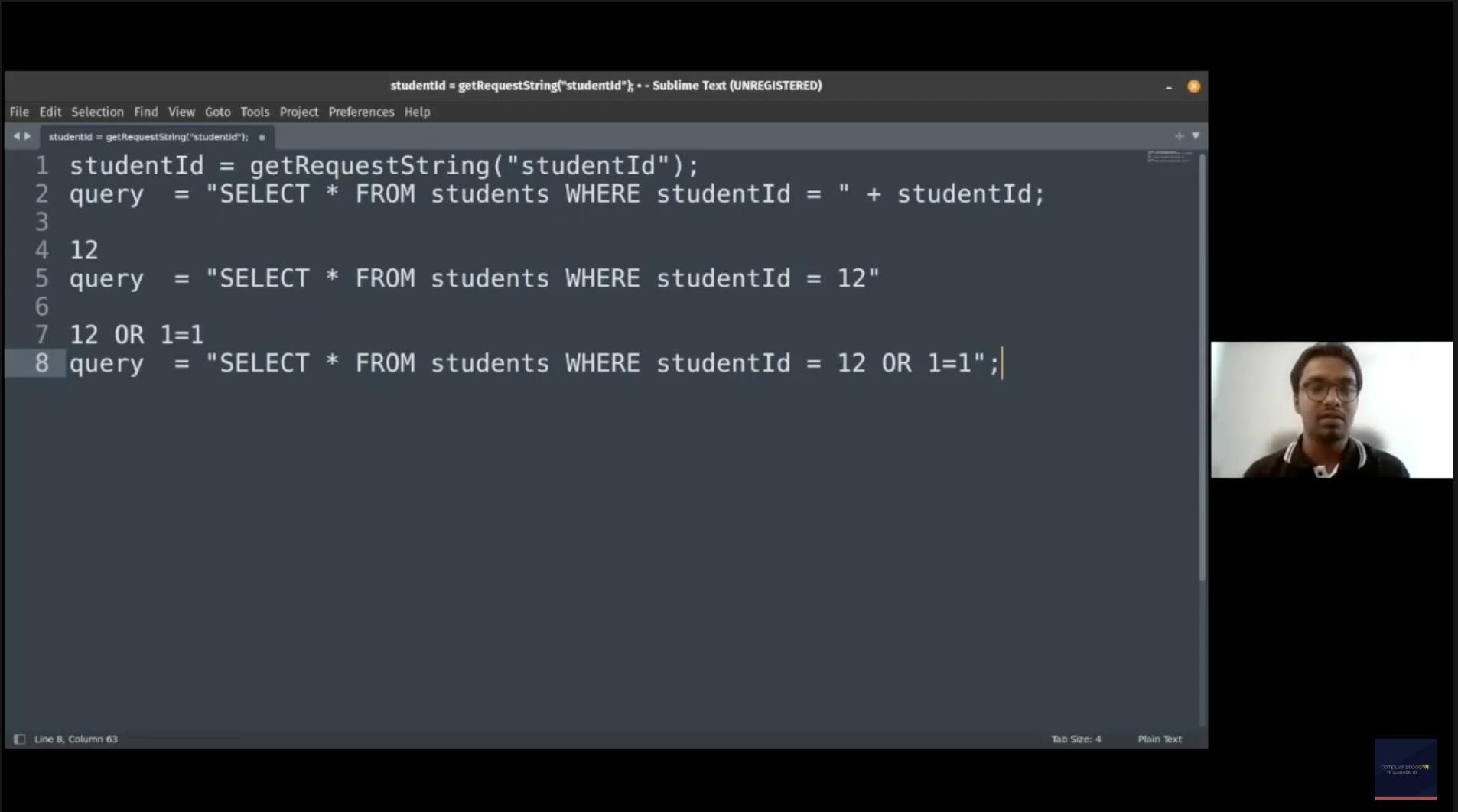
This demonstration of SQL injection had shocked me because of how simple and dangerous it can be, what's happening here is that the attacker is passing the input such that it can be true for all students, he's using the OR logical operator and passes another input "1 = 1" and this input becomes true for all the students and hence he gets access to the records of all the students with a single input. This can be very dangerous when sensitive information is being targeted. Using an ORM (Object-Relational Mapping) can sometimes secure us from injection attacks.
Next, we moved on to the OSWAP Mobile Top 10 List, that listed the top 10 vulnerabilities in mobile applications, here we took a deep dive into one of the vulnerabilities, Insecure Data Storage. This was explained with the example of a bug that Tinder had during its early days, where the information regarding the user location can be tracked by anyone with just their tinder ID.
Another famous vulnerability is information disclosure, this is when an application unintentionally leaks any kind of user information to third parties, hence causing a threat to the user's privacy.
Next, we discussed the reasons for why mobile apps are targeted and as we moved further into this discussion, we were introduced to BeVigil, BeVigil is a security search engine for mobile applications. Mr. Sudipta gave us a quick tour through this amazing platform , he initially searched for an app and found it, after he clicked on the app, BeVigil listed a bunch of fancy tabs containing vulnerabilities along with a lot of other information and with a security rating out of 10. This was so cool, it felt magical, it was like taking a master health check-up for a human being but for a mobile app, it listed all the loop holes that the app had. After introducing us to this marvelous application, we were asked to go for lunch and explore the rest about this in the hands-on session.
The Hands-on Session
Everyone returned from lunch, fully recharged for what was to come in the hands-on session. Here, we learnt more about the BeVigil platform and Mr. Shahrukh guided us through the platform in an easy to follow pathway, he also demonstrated a vulnerability finding on an app from my college, this app is used by all college students. This sparked my curiosity more and I wanted to check out the security rating on some of the apps on my phone, when the app I searched wasn't there, I recalled when Mr. Shahrukh told us that we can scan our own apps and get the report instantly, when I tried this myself, I was amazed by how quickly BeVigil had scanned my app and gave me the security rating along with other briefings.
But I wanted to see if an app had a lesser security rating, and I wound the app, it was the PicsArt app, it's the app I use when I want to quickly edit some photos. I searched for the app and already found it on the platform.
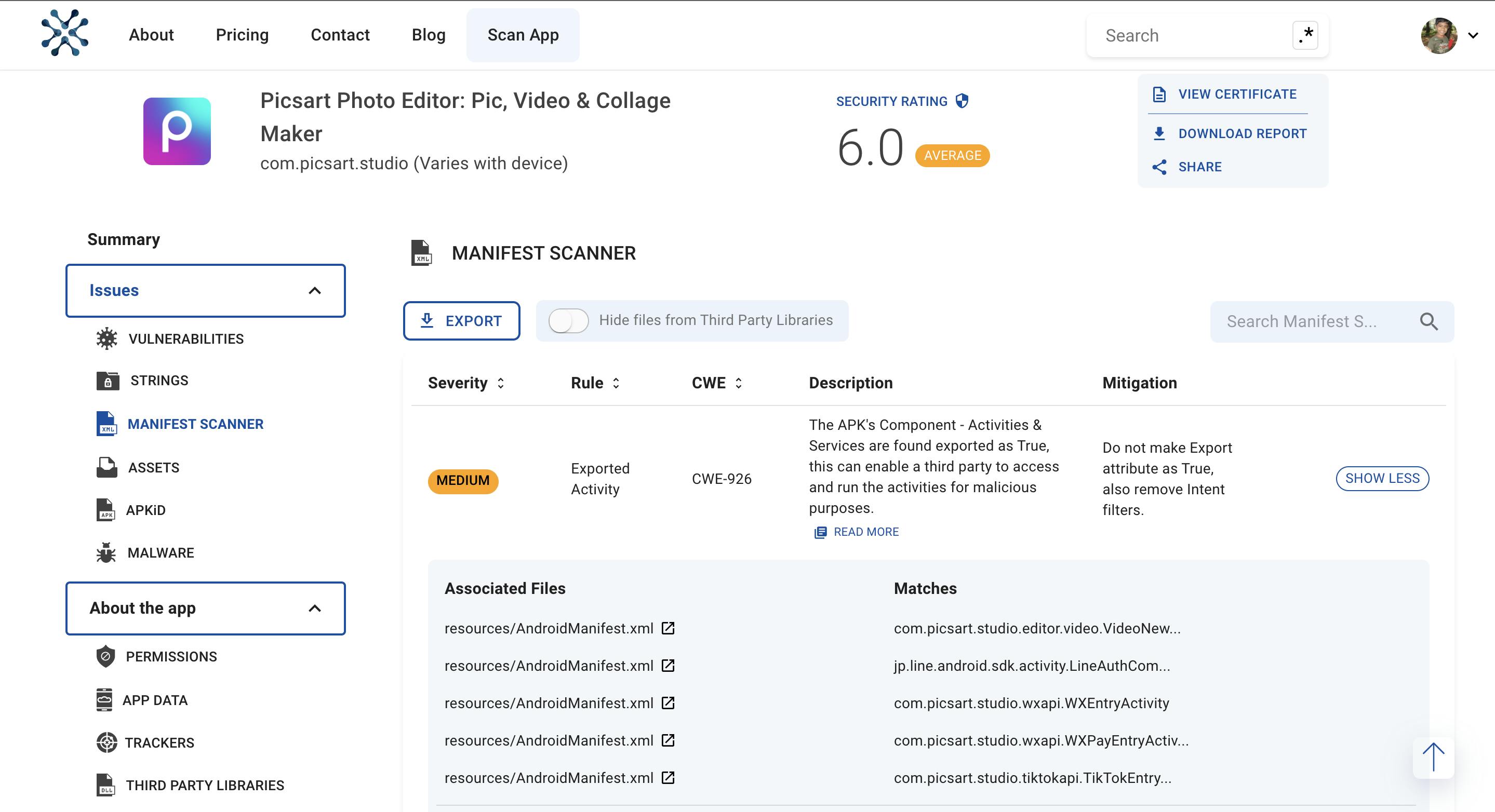
Here's a screenshot from how things look like when we deep dive into an app in BeVigi. I was quite surprised at how an app so popular and has been used by many for years had a security rating of just 6.0, so I decided to take a deep dive into this app and discovered that the vulnerabilities ranged from low to medium level and there were no high level vulnerabilities present. As I was searching up more about a few of my findings that seemed suspicious, I realized that there were so many things to take in at once and most of them seemed a little too complex for my current understanding but none the less, it was exciting to see that there was so much more to learn and explore. Since exploit hunting was new to me, my attempts to report the exploits properly were in vain as I couldn't take advantage of an exploit properly, but the process of finding these exploits in itself was a very interesting one filled with lots of learning and it kept me going.
Wrapping up!
Although I couldn't submit a proper report, I learnt so much in the process and had got exposed to so many new terminologies and technologies that are being used by app developers and security researchers across the globe. If anything this has gotten me even more curious to do more research on the topic and find some more interesting stuff. So it was a great experience overall. Another advantage I had got from being a part of this workshop is that , I had not only learnt about things related to vulnerabilities, bugs or technical reporting but also the other topics that linked to these, some of these topics involved concepts that I would be learning for the future course in my degree and it was a great introductory path to dive into these. I had a great experience exploring apps using BeVigil and I'm glad to have been a part of BugéDex and I'd like to express my thanks to CloudSEK and CSI-VIT for organizing this fun and insightful workshop.
I'll end my blog with a group photo from the workshop :D !